BootHole is a newly discovered security vulnerability that affects Linux systems using UEFI Secure Boot feature. The vulnerability allows full root access once exploited in the host system.
Patches across many different Linux distributions were shipped before the weekend to fix the security issue. However, after applying the patches and rebooting their systems, many users are reporting that they are unable to boot their systems at all.
Various Linux distributions were affected differently by the update due to the nature of their components. Some of them failed only with UEFI Secure Boot systems, where as others failed only with legacy BIOS systems.
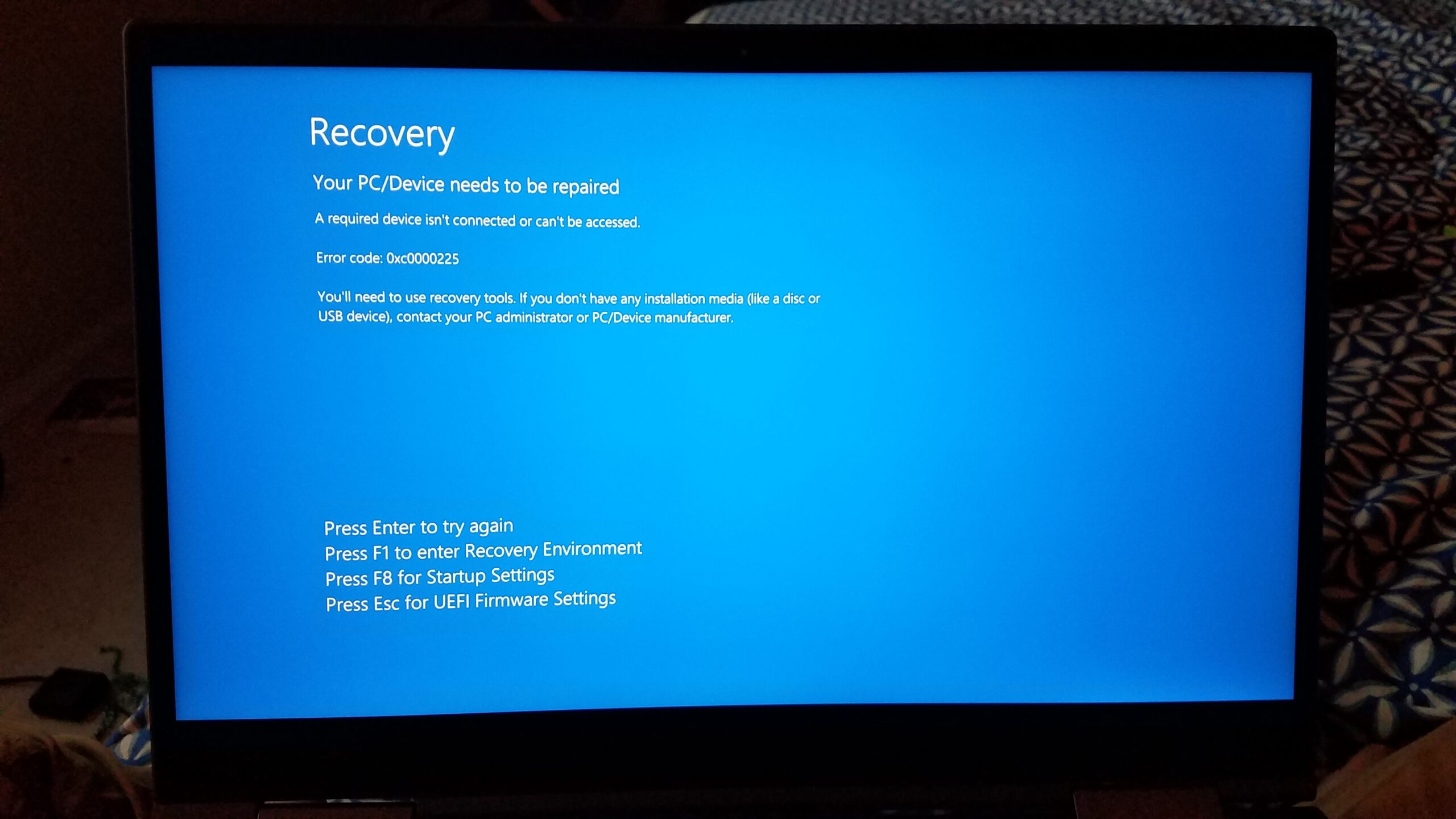
However, the issue is more critical, because it also affects cloud/DevOps systems such as Hyper-V, Amazon EC2, Microsoft Azure and most virtual machine providers.
The status of the current scene is as follows:
- Red Hat/CentOS/Fedora: All affected, both UEFI Secure Boot and legacy. Red Hat released an update which fixes the issue, however, they still classify it as “unverified” so more testing is needed to make sure it works. It is worthy to note that Red Hat was the first to catch the issue, but the last to patch it,
- Ubuntu/Debian: Many users are reporting that the bug only affects the BIOS-powered boot systems, and not these running UEFI Secure boot. However, a fix was released anyway and users can safely upgrade.
- openSUSE/SUSE: The original patch caused no regression at all for most users. However, some users reported that the update caused a regression for their systems, but that is still yet to be checked. SUSE hasn’t released an update to fix a regression (Didn’t even mention discovering it).
- Gentoo/Arch: No reports were sent about a regression, users can safely upgrade.
Honestly speaking, this is a major fail for most Linux distributions, because had this happen on Windows, Linux users would have memed Microsoft for years to come about it. A deep look is needed on why no QA team across all Linux distributions was able to catch the issue before releasing the upgrade for the world, especially enterprise distributions like Red Hat.
One can also be more concerned about novice users, who don’t know how to downgrade packages or fix the issue once it happens on their systems.
FOSS Post is a high-quality online magazine about Linux and open source software. With a team of professional writers from all over the world, we bring you the latest articles, analysis and reviews related to open source.
Articles published with this account are written as a collaborative effort between writers. You can email us at contact@fosspost.org