GNOME Software is the default application in the GNOME desktop environment to manage software. It also allows you to receive firmware updates through an underlaying daemon called “fwupd“, which is based on an platform called “LVFS“.
In order to understand the relationship in a clearer way, you can think of LVFS as the online platform where hardware vendors come and upload new versions of their firmware which will be later available to download via fwupd. GNOME Software utilizes the fwupd daemon in order to download and install these updates. fwupd is a dependency for GNOME Software.
The whole ecosystem is developed mainly by Richard Hughes, who is working currently for Red Hat, and who’s also the original creator of PackageKit. But it’s worthy to mention that Red Hat doesn’t develop/manage the project directly, but rather, contributes to it with financial & logistic support.
Table of Contents:
The Privacy Concern
fwupd is an integrated part of GNOME Software. In order to be able to receive updates for firmware available in your computer, fwupd retrieves a metadata file from fwupd.org (which is named LVFS) and matches on client-side to see if there’s an update to that firmware or not. If there’s an update, the firmware file will be grabbed and installed from fwupd.org.
Additionally, fwupd (upon each checking for updates in GNOME Software) sends your machine ID (hashed), IP address, current Linux distribution name and version and client user-agent to fwupd.org.
According to fwupd.org/privacy, some parts of this data is being shared by 3rd-party hardware vendors, who may be interested in the number of people downloading these updates and what kind of Linux distros they are using. IP addresses are not shared, but client user-agent & hashed machine IDs are. This privacy policy is guaranteed by the developer himself, not a company or an organization:
As the Data Protection Officer, Richard Hughes has overall responsibility for the day-to-day implementation of this policy. The DPO is registered with the Information Commissioner’s Office (ICO) in the United Kingdom as a registered data controller.
The issue here is that in GNOME Software, users have no idea that such data is being sent or collected. An ordinary user does not expect his software center to be downloading updates from an online website without telling him so. Upon opening GNOME Software for the first time, no privacy policy is displayed and no message informs the user that such data is used and sent to fwupd.org in the first place.
There’s no indication when using GNOME Software that fwupd.org will be used to update the firmware packages.
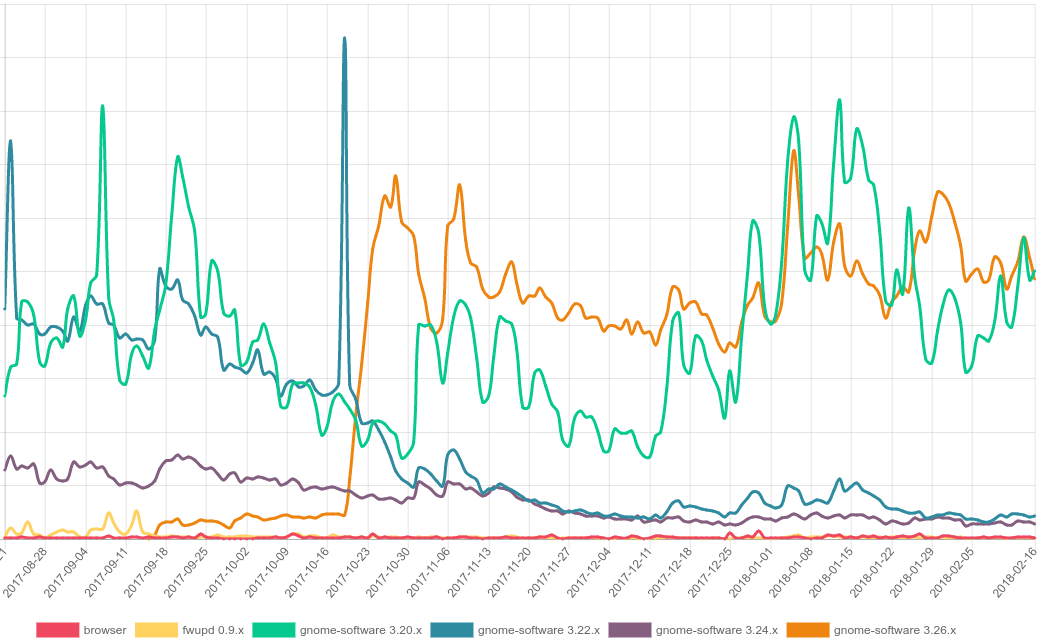
Currently, the main developer behind GNOME Software announced that 100 million files are being downloaded from fwupd.org each month. Most of them are metadata files. This is due to the fact that both GNOME Software & fwupd are installed by default on all modern major Linux distributions, such as Ubuntu and Fedora. The developer was able to produce the following chart from the data he has:
This is a huge amount of data and accessibility available about Linux users under the hands of a single developer. The collection of such data should be opt-in, not opt-out by default in order to respect the privacy of users who don’t want to use the fwupd.org service to check for firmware updates. More importantly, at least, the privacy policy related to the collection of this data should be displayed on the first use of GNOME Software. Otherwise, users won’t know that such data is being sent.
The other issue is that up to few weeks ago, there was no way to disable fwupd integration in GNOME Software. It was just after version 3.26 (not included) that the developers added an option in the settings page to disable fwupd service. Before that, you were forced to use fwupd if you are using GNOME Software. You can’t even disable it (graphically).
According to the developer, fwupd.org is hosted on Amazon EC2. Amazon (beside many other companies as well) has donated $2000 per year to develop the project, and provides some hosting features for free as well. fwupd.org domain name is registered in the personal name of the project’s developer (if you check from who.is).
The privacy policy page mentions that the metadata users send to fwupd.org is stored up to a maximum of 5 years:
Anonymized user data (e.g. metadata requests) will be kept for a maximum of 5 years which allows us to project future service requirements and provide usage graphs to the vendor.
The developer says that the IP addresses are not stored on fwupd.org. But sadly, since this is a server-side claim, there’s no way as users to confirm such claim. Also, the machine ID collected from users’ /etc/machine-id is said to be hashed (with salt) before sharing it with vendors.
A single bottleneck for manging the hardware data of the entire Linux desktop users wouldn’t be a good idea.
A Security Concern
fwupd.org allows hardware vendors to create an account by emailing the project’s founder. Then, vendors can get information about the number of users of their hardware and what operating system & client they are using. Vendors can push .cab files to users to be downloaded later by GNOME Software. These .cab filed are claimed to be tested by a separated QA team before released to users.
The security issue is in maintaining the infrastructure for fwupd.org. If hacked, thousands of daily requests to the server and the data available could be leaked. The team behind fwupd.org claims that there are many professional teams working on securing the platform according to the industry’s best practices. However, a user can not guarantee.
We couldn’t find reports or sources on how many people in total are behind the whole project, or how many people are reviewing the pushed .cab files by vendors. The metadata stored in fwupd.org are said to be stored under a locked LUKS filesystem hosted on Amazon.
The other concerning issue is that the developers are not 100% financially covered. There has been multiple calls for donations by the developers:
At the moment the secure part of the LVFS is hosted in a dedicated Scaleway instance, so any additional donations would be spent on paying this small bill and perhaps more importantly buying some (2nd hand?) hardware to include as part of our release-time QA checks.
And another one:
The current CDN (~$100/month) is kindly sponsored by Amazon, but that won’t last forever and the donations I get for the LVFS service don’t cover the cost of using S3. Long term we are switching to a ‘dumb’ provider (currently BunnyCDN) which works out 1/10th of the cost.
Which could rise questions about the future of the ecosystem managing 100 million requests per month.
A Suggested Solution
We believe the following should be taken into consideration to solve the issues above:
- GNOME Software should detach fwupd as a dependency. Because if fwupd package is installed, it will auto-check for updates in the background (fwupd daemon will autostart after boot) and it will send the data to fwupd.org automatically.
- GNOME Software should disable the service of using fwupd.org for firmware updates by default. Users wishing to subscribe to such service should opt-in their selves.
- Upon activation of fwupd service, a privacy policy dialog should be displayed telling users about what’s going to be collected and why.
- The project’s domain name and infrastructure should be managed and ran by an organization/company. More detailed information on who’s accessing the infrastructure and working on it should be available.
The Bottom Line
Here, we do not try to question the sincerity or the authenticity of the project’s developers, but we seek to let users know what’s happening under the hood of their software center. We also believe that such infrastructure should be more transparent in the way it’s secured and managed, and how the data is stored and accessed.
In result, this ecosystem will have access to millions of Linux machines worldwide, and putting all the eggs in one basket is a concerning thing. We believe that such model was implemented with good intentions in the sole reason of serving users, for free. But privacy is becoming a very important issue. especially these days with the so-called hijacks of data around the world.
At the end, we would like to thank Richard and all others for their work on free/libre software.
Update @ 14 Apr, 03:49: The developer clarified that the hardware information of a user doesn’t get sent to fwupd.org. As such, this article was updated.
Update @ 18 Apr, 19:12: To clarify this even more, firmware matching for updates is done on client-side, not server side, meaning that GNOME Software (or fwupd) does not send hardware information to fwupd.org as this article said initially. This claim was online for around 10 hours after publishing the post before it was taken down. We would like publicly to apologize for Richard and anyone who read the article in that period for making such claim without making sure of it first.
However, it’s extremely important to also say publicly that this article (in its current form) is valid and true. GNOME Software (fwupd) was confirmed to send client user-agent, IP address, timestamp, OS distribution name and OS version to fwupd.org upon each firmware downloading process (or checking for firmware updates manually by the user). Sending 5 forms of data instead of 6 doesn’t mean that the whole thing is false. The connection to fwupd.org to provide the firmware updating service is a place of concern because it doesn’t belong to the user nor the Linux distribution’s makers (Ubuntu, Debian, Fedora, openSUSE..) and happens without users even knowing. Users knowing of this service is important, and is the main point of this article.
Just 2 days ago, and after 48 hours of publishing this post, the developers have pushed a commit to the GNOME Software code titled: “Add a warning when enabling the LVFS remote”. Here’s the commit message:
Distributions like RHEL do not enable the LVFS by default and the legal team here say we need to add some agreement text which is shown before we enable downloading content from an external source.
These concerns has no relationship to the quality or work of the LVFS project itself. Being able to update the BIOS on a Linux system without needing Windows is a huge achievement. This article doesn’t say that fwupd (or GNOME Software) is bad, or poorly written or should not be used, but discusses “concerns” related to privacy & security, nothing more and nothing less.
With a B.Sc and M.Sc in Computer Science & Engineering, Hanny brings more than a decade of experience with Linux and open-source software. He has developed Linux distributions, desktop programs, web applications and much more. All of which attracted tens of thousands of users over many years. He additionally maintains other open-source related platforms to promote it in his local communities.
Hanny is the founder of FOSS Post.