WAF or Web Application Firewall is a software that provides additional protection to the working web application or web server from possible attacks when it becomes connected to the Internet. Just as you can guess from its name, it is similar to how a system firewall works, with the exception that it only protects the web application and not all of the system connections.
WAFs are useful to protect against common HTTP hacking techniques such as SQL injections, cross-site scripting and CSRF attacks. They can also provide defense against distributed denial-of-service attacks (DDoS).
Instead of having users directly connecting to your web application, the WAF will instead sit between the user and the web application and filter requests according to how it was programmed and tweaked. In this way, you remain protected from possible threat actors.
Table of Contents:
What are the Benefits of Using an Open Source WAF?
Just like any software category, web application firewalls are divided into commercial proprietary solutions and open-source WAFs that can be self-deployed.
The benefits of using an open-source WAF to protect your web application include:
- Saving costs since most of these firewalls are also free of charge. You won’t need to be for a premium recurring subscription just to use them. Some proprietary WAF providers like Cloudflare may block you from their service if you exceed a certain threshold of requests.
- Privacy because your customer connections and data don’t need to be sent into a 3rd-party for analysis and to provide the security you seek. Instead, they will run locally on your machine.
- Customizability since the source code is open source and you can modify it or tweak it according to your own needs and the web application you want to protect.
- And of course, the additional security to your service that you will gain after setting up the WAF.
The only possible con to using these types of software is that you would need to set them up on your own and waste some time and effort with them. Or if you are not ready to do that, then you will have to pay for a 3rd-party vendor to provide support services for you.
Top Maintained Open Source WAFs
We are going to see the top open source web application firewalls that are still being maintained so far. You can select between them according to your web application needs and other features that might interest you.
We made sure to select only the top working, still-maintained and useful software that belong in this list for our readers. You can review our criteria for listicle articles on FOSS Post to understand the basis for our selections. Remember that we only cover open-source software on FOSS Post that follow the OSI definition and an OSI-approved license. The ranking is random and does not reflect our rating for the software.
1- SafeLine
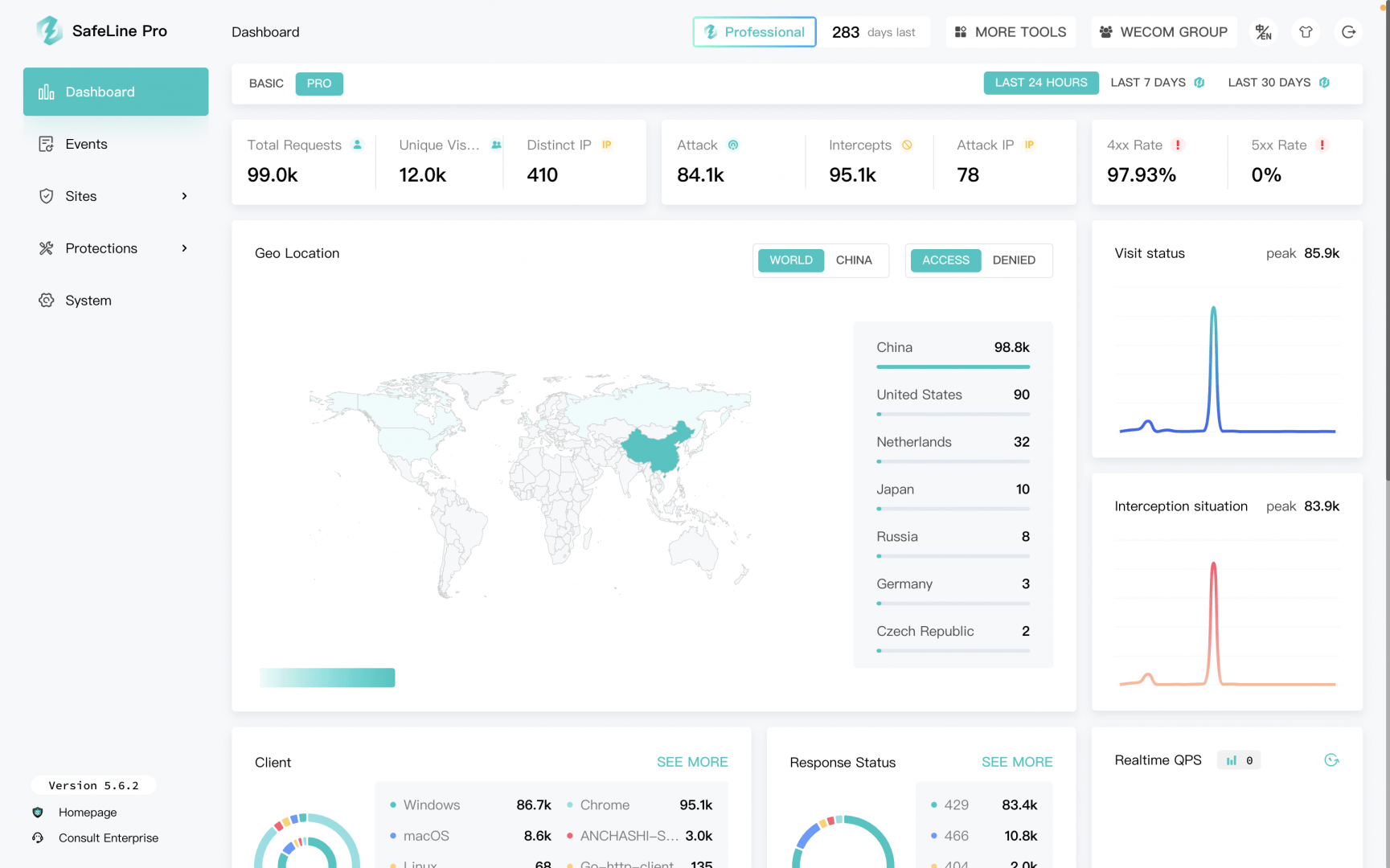
SafeLine is a reverse proxy designed to effectively protect web servers/applications from various attacks and exploits. Developed based on Nginx, SafeLine offers a lot of defenses against numerous types of threats such as SQL injection, code injection, OS command injection, CRLF injection and others. Its core capabilities include bot abuse defense mechanisms such as HTML & JS code encryption and IP-based rate limiting. Additionally, it provides robust Web Access Control List (ACL) functionalities to tweak according to your needs.
What sets SafeLine apart is its seamless integration with existing infrastructures while providing extensive protection features without significant performance overheads. The software supports automated deployment via simple bash commands or using Docker as a container.
Users can manage their protected sites using a very modern web admin interface that allows real-time monitoring and management of the WAF, which makes it suitable even for novice system administrators or web developers.
- Software license: GPL-3.0.
- Programming language: Go, C++, Perl and Lua.
https://github.com/chaitin/SafeLine
2- Open-appsec
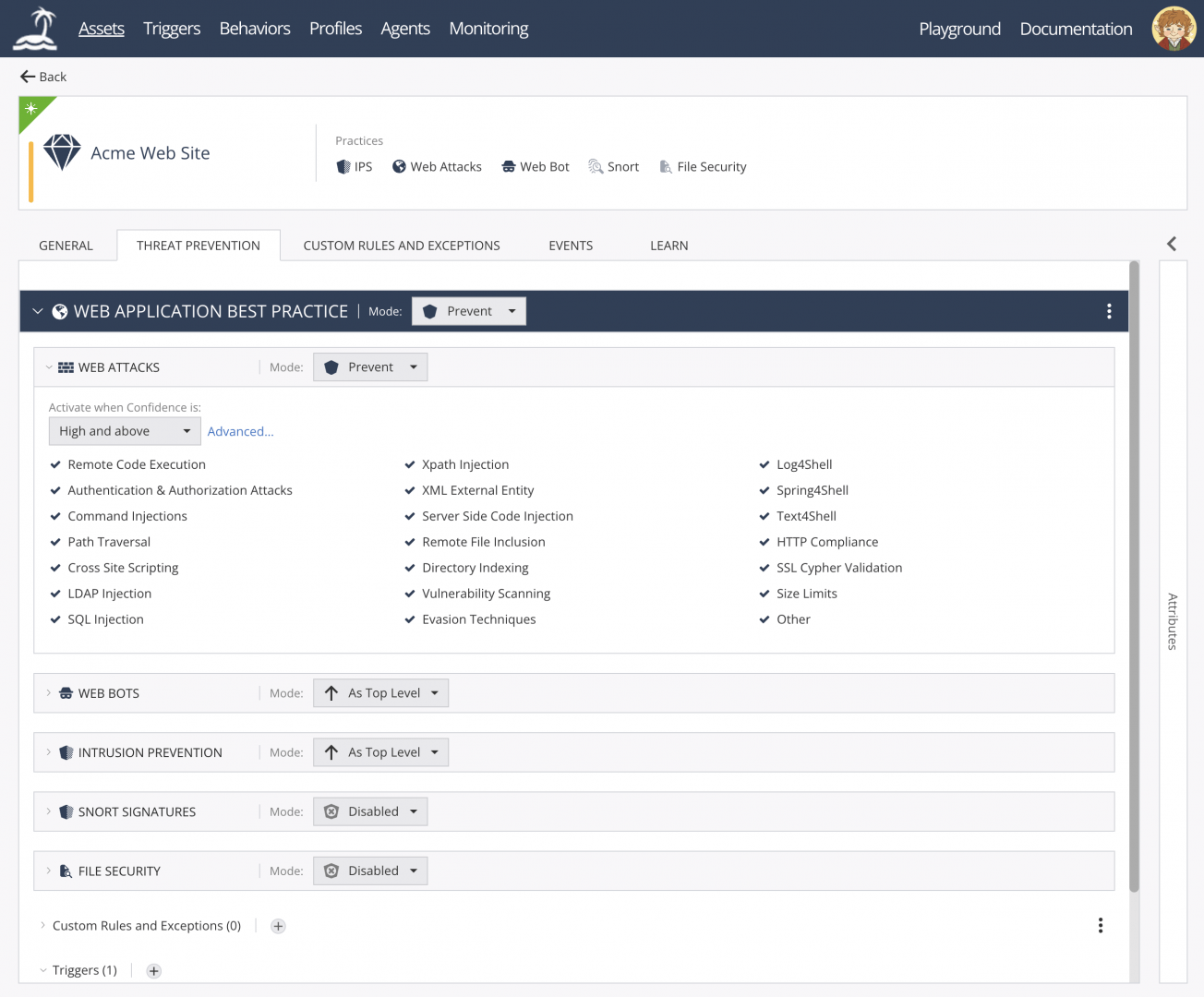
Openappsec is a machine learning security engine designed to prevent threats against web applications and APIs. Written primarily in C++, it leverages both supervised and unsupervised AI models for threat detection, focusing on preventing OWASP Top-10 vulnerabilities as well as zero-day attacks. The software can be integrated with Kubernetes Ingress, NGINX, API Gateways and others. Its core functionality involves analyzing HTTP requests by decoding all parts of the request payloads including JSON/XML sections while applying IP-level access control measures.
The system operates through two models: initially employing a globally-trained supervised model that evaluates multiple variables extracted from each HTTP request such as attack indicators or user agents, followed by an environment-specific unsupervised model which uses real-time traffic patterns unique to your deployment setup for further analysis if necessary.
This dual-layered approach ensures high accuracy in identifying legitimate versus malicious activities within network traffic flows. However, it could be resource-heavy due to the AI features it employs, so tread carefully with it.
- Software license: Apache 2.0.
- Programming language: C++.
https://github.com/openappsec/openappsec
3- ModSecurity
ModSecurity is an open-source, cross-platform web application firewall (WAF) engine that works with Apache, IIS, and Nginx web servers. It features a robust event-based engine that offers protection against various attacks on web applications while enabling HTTP traffic monitoring, logging, and real-time analysis. The software has undergone significant architectural changes to remove dependencies on the Apache server in its newer version (v3), resulting in enhanced performance across different platforms.
Written primarily in C++ with compliance to the C++17 standards, ModSecurity utilizes several libraries to do its job. The nice thing about is that its modular design allows integration to each platform like Nginx or IIS, which are maintained separately from the core library codebase known as Libmodsecurity. In other words, the WAF can be integrated into any of the mentioned web servers or even to any other compatibile software.
Sadly, it does not provide a ready user interface for the user out-of-the-box. So you will have to use it from the command-line all the time when you want to utilize it.
- Software license: Apache-2.0
- Programming language: C++.
https://github.com/owasp-modsecurity/ModSecurity
4- BunkerWeb
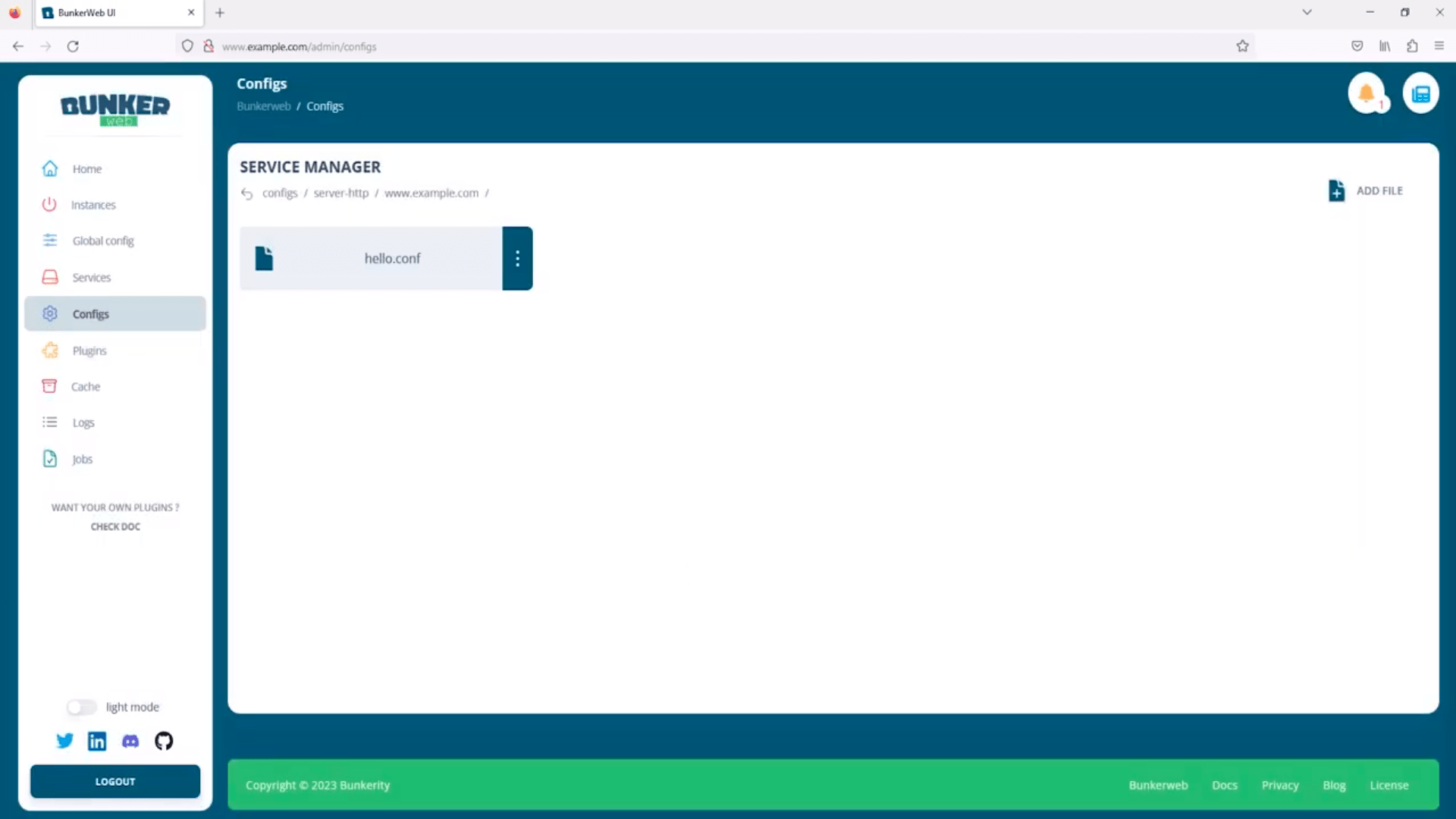
BunkerWeb is yet another web application firewall. It uses NGINX at its core inside a Docker container to integrate seamlessly into various environments, including Linux, Docker, Swarm, Kubernetes, and Microsoft Azure. The software supports a wide range of security features such as HTTPS with Let’s Encrypt automation, HTTP security headers for preventing data leaks and TLS hardening. Additionally it includes ModSecurity WAF integrated with the OWASP Core Rule Set for enhanced protection against common threats.
A key aspect that sets BunkerWeb apart is its high level of customization through settings and plugins which can be managed via a user-friendly web UI. Users can have access to extendable functionalities and get plugins like ClamAV antivirus and others supported officially within their plugin repository.
Users can choose to either self-host the software, or used their ready cloud service called “BunkerWeb Cloud” that is similar to Cloudflare WAF to block possible threats. Of course, the latter costs money.
- Software license: AGPL-3.0.
- Programming language: Python.
https://github.com/bunkerity/bunkerweb
5- Coraza
OWASP Coraza WAF is an open-source, high-performance web application firewall (WAF) written in Go. It supports ModSecurity SecLang rulesets and is fully compatible with the OWASP Core Rule Set v4 to protect applications from a wide range of attacks such as SQL Injection (SQLi), Cross-Site Scripting (XSS), PHP & Java Code Injection, HTTPoxy, Shellshock among others. The software offers extensibility through various integrations for deploying on-premise instances and allows users to create custom functionalities via audit loggers or persistence engines.
Key features include its drop-in capability replacing Trustwave’s ModSecurity Engine while maintaining industry-standard security measures with minimal false alerts.
Sadly, this one also does not provide a web UI that you can access to control the WAF, so you are left with the command line if you want to tweak it or view its log files.
- Software license: Apache-2.0.
- Programming language: Go.
https://github.com/corazawaf/coraza
Conclusion
These are the top open-source WAF software that are still being maintained in the market. There are many others that you could possibly find on GitHub and other platforms, but them being not maintained/archived is why we omitted them from this list.
Remember that using a WAF to protect your web application does not mean that you have %100 security; no such thing exists, and if your web application is buggy or contains a unique security vulnerability, then the WAF may not be able to detect it.
It remains your responsibility to ensure the security of your service and your users’ data via all possible methods, including hiring security professionals and pentesters to evaulate your web service.
FOSS Post is a high-quality online magazine about Linux and open source software. With a team of professional writers from all over the world, we bring you the latest articles, analysis and reviews related to open source.
Articles published with this account are written as a collaborative effort between writers. You can email us at contact@fosspost.org











Wanna leave a comment on this story? Check it out on our Outpost forum and participate in the conversation.
Leave a Comment